What is PUP.Driver Updater?
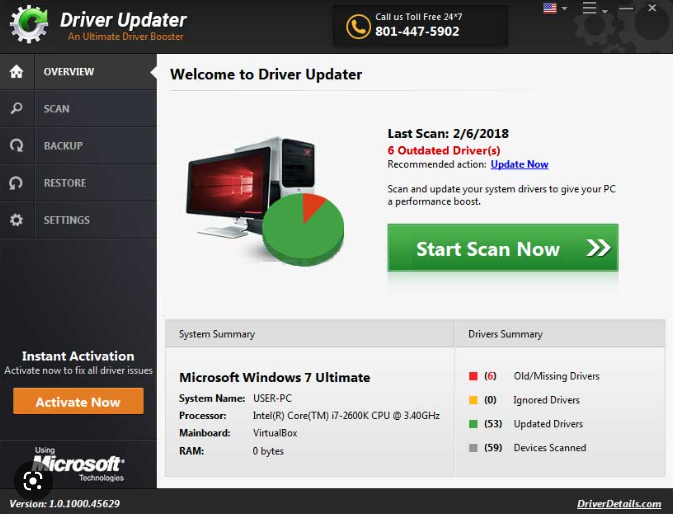
PUP.Driver Updater is the detection name anti-virus programs use to detect potentially unwanted program (PUP) Driver Updater. While Driver Updater is not a malicious program, its installation methods as well as dubious scan results have resulted in the program being classified as a PUP. It uses deceptive means to promote its paid version, primarily by showing exaggerated scan results. The program scans for drivers that need to be updated for free but requires a subscription to update them. The program makes it seem like the computer’s performance will be improved if they use it, though that is unlikely to be the case.
It’s a program that can install through software bundling, so users may not even realize when PUP.Driver Updater installs. If you suddenly discover something on your computer that you don’t recall installing, it was probably installed via the software bundling method. To put it simply, PUP.Driver Updater may have been attached to some free program you installed as an extra offer. These offers are permitted to install alongside the programs they’re attached to automatically. This will be covered in more detail later on in this report. Programs that use it are almost always labeled as PUPs at the very least because it is a somewhat misleading installation technique.
Soon after installation, PUP.Driver Updater will begin displaying notifications that you need to scan your computer. If you use Driver Updater to scan your computer, the results may be quite alarming. The program may claim that there are tens or even hundreds of issues related to drivers that need to be fixed immediately. You will only be able to scan your computer with the free PUP.Driver Updater version. To fix the detected issues, the program will ask that you first buy a subscription. While asking for users to pay for subscriptions before allowing them to use all features is nothing unusual, PUPs like Driver Updater display fake or exaggerated scan results to pressure users into making purchases. Evidently, this is a deceptive tactic.
The primary function of PUP.Driver Updater is installing driver updates but most users do not need this function. Even if you determine that you need to update your drivers, you should only download drivers from the websites of the manufacturers. Additionally, all necessary driver updates are typically installed through Windows updates, negating the need for additional action. There’s really no need to use system utility tools like Driver Updater, especially ones that you need to pay for. Purchasing Driver Updater would be a waste of your money. As a result, we strongly advise you to remove PUP.Driver Updater from your computer if it’s detected on your computer.
However, it should be mentioned that even though it’s frequently referred to as a virus, PUP.Driver Updater is neither a malicious nor a harmful program. Nevertheless, it serves no purpose so keeping it installed is not recommended.
How did PUP.Driver Updater install on your computer?
Since PUP.Driver Updater has an official website and is accessible for download from third-party websites, it’s not impossible that you downloaded and installed it on your own. However, a quick Google or other search engine search would have returned numerous results warning about using PUP.Driver Updater. In the future, we advise researching programs before downloading them to avoid installing unwanted or even malicious programs.
However, the program was most likely installed via the software bundling method. Software bundling is a rather deceptive installation technique, which is why it’s so controversial. Software bundling basically involves adding extra offers to programs. These offers could be anything, but they frequently are adware, browser hijackers, and potentially unwanted programs. Although they are optional, the manner in which they are added enables the offers to be installed automatically without requiring any explicit authorization from users. Additionally, the offers are initially hidden, and users need to use specific settings to even see them. This is why users are often unaware of these installations and are taken by surprise when they start seeing unknown programs on their devices. However, the offers are not difficult to deselect, as long as you know how to correctly install freeware.
Selecting Advanced (Custom) settings while installing free software is very important. Default settings will be recommended by the installation window but using these settings will lead to all added offers being installed on the computer automatically. Unlike Default settings, Advanced settings will show every offer added to the program. Additionally, you will be able to uncheck all of them. Simply uncheck the boxes of those offers. This should be done with every free program you install. Otherwise, your computer will quickly become overrun with useless programs. Furthermore, preventing their installation is considerably simpler than having to uninstall them once they’ve been fully installed.
How to remove PUP.Driver Updater
If you are using ESET, Malwarebytes, Windows Defender, or any other legitimate anti-virus program, they should be able to remove PUP.Driver Updater for you since several anti-virus providers have identified the application as a PUP. It is also possible to manually remove PUP.Driver Updater, however doing so may require more effort and time since you would have to do everything yourself.