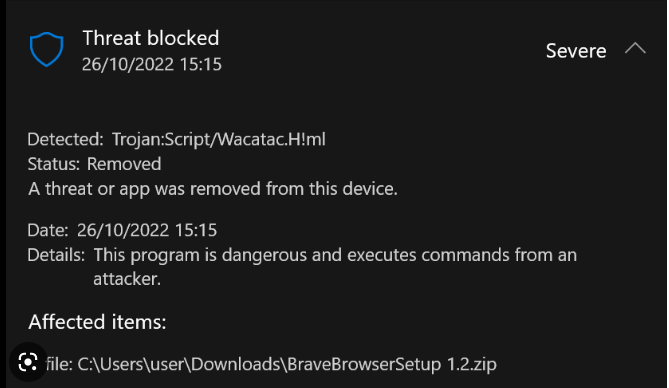
What is Wacatac Trojan
Wacatac Trojan is a trojan infection that enters computers in a stealthy way and can remain unnoticed for a while if an anti-virus program is not installed on a computer. Once on a computer, the trojan can do a lot of damage, including allowing other malware to enter, stealing passwords and other sensitive information, adding your device to a botnet, etc. In many cases, trojans can remain unnoticed for a long time because they show no signs of being present. This allows them to carry out their malicious activities for a long time.
Wacatac Trojan being present on your computer may lead to your passwords and other sensitive information being stolen. This information is a hot commodity, and once it gets stolen, it ends up on hacker forums where other cybercriminals buy it for their own malicious purposes. Trojans can also steal information like payment card details or online bank login credentials, which could potentially lead to financial loss.
Trojans can also work like backdoors for other malware to get in. Such an infection may lay dormant for some time until malicious actors buy access to your device and infect it with other malware (e.g. ransomware). If the trojan allows a ransomware infection to enter your computer, your files would be encrypted. Ransomware is one of the most serious infections you can encounter because once files have been encrypted, it will not necessarily be possible to recover them.
If anti-virus software is not installed on a computer, it can be difficult to detect a trojan like Wacatac on a computer. There may be some signs but users need to be aware of them to be able to identify them. Some of the most obvious signs include programs failing to launch or crashing all the time, the computer lagging without any apparent reason, and unknown processes appearing in Task Manager. However, it’s strongly recommended that you have anti-virus software installed on your computer so it can detect malware. If you want to protect your computer and data, you need to have an anti-virus program installed.
How did Wacatac Trojan enter your computer?
Trojans are distributed in a variety of ways, and it’s important that users are familiar with at least the most commonly used ones. Being familiar with those methods will allow you to avoid quite a lot of malware in the future.
Wacatac Trojan is known to be spread via software cracks. Users who pirate programs because they do not want to pay for premium versions are at a high risk of encountering malware. In general, users who pirate any kind of content will encounter malware sooner or later. For example, torrent websites are often full of malicious torrents. In particular, torrents for entertainment content (e.g. movies, TV series, software) often have malware. If users do not know how to recognize malicious torrents, they will easily end up with malware without even realizing it. Pirating copyrighted content is also essentially content theft, so it’s highly discouraged.
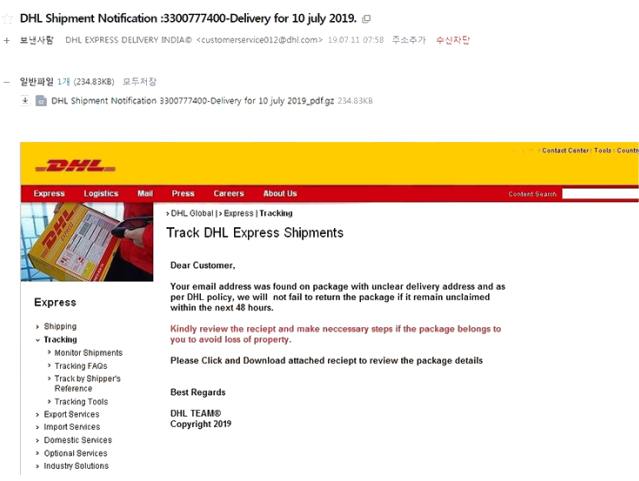
Email attachments are one of the most common ways that cybercriminals spread malware. It is a pretty easy method of distribution for cybercriminals because it requires little effort. Malicious actors buy leaked email addresses from hacker forums and then use them for their malware distribution campaigns. These email campaigns have malicious files attached, and when users open those files, they end up infecting their computers with malware. Fortunately for users, malicious emails are quite obvious most of the time because they have very little effort put into them. The emails usually have a lot of grammar and spelling mistakes. Because senders frequently claim to represent legitimate companies, the mistakes stand out quite a lot. Grammar/spelling mistakes in legitimate emails look very unprofessional so they are avoided.
When a sender who should know your name uses words like “User,” “Member,” or “Customer,” to address you, it may also be a red flag. Emails from legitimate companies to their customers will always address users by name because it makes the email seem much more personal. Malicious actors rarely have access to their targets’ personal information so they use generic words to address them.
Finally, it’s important to note that some malicious emails might be far more sophisticated. Therefore, it is recommended to check all unsolicited email attachments for malware using VirusTotal or anti-virus software before opening them.
How to delete Wacatac Trojan
If you know that Wacatac Trojan is present on your computer, you likely already have an anti-virus program installed. Allow it to delete Wacatac Trojan from your device. You should also keep the anti-virus program fully running on your device at all times in order to detect malware infections before they can do any damage.
We recommend avoiding trying to remove Wacatac Trojan manually because it’s a fairly sophisticated infection and manual removal could cause additional issues.
Wacatac Trojan is detected as:
- Win32:CrypterX-gen [Trj] by AVG/Avast
- Trojan.Zmutzy.Pong.2 by BitDefender
- Win32/PSW.Fareit.A by ESET
- Trojan.Win32.VBKryjetor.bzrz by Kaspersky
- PWS:Win32/Fareit by Microsoft
Because trojans are capable of stealing passwords, it’s a good idea to change all your passwords once you remove Wacatac Trojan from your computer.
Prevent future cyberatacks attacks
Anti-malware program SpyWarrior uses artificial intelligence technology to effectively deal with ransomware attacks. Known ransomware strains will be immediately detected and blocked before they can do any damage or encrypt files. And if the ransomware strain is new, its suspicious behavior would still be detected, and the attack would be stopped in time.
