What is ransomware
For those fortunate enough to not have heard of ransomware, it’s a type of malware that encrypts files, making them essentially useless. To put it simply, ransomware holds files hostage until a ransom is paid. To decrypt the encrypted files, it’s necessary to pay money, aka a ransom. It’s a highly complicated malware infection that can do and has done significant damage. It is estimated that ransomware will cost around $6 trillion in damages in 2021.
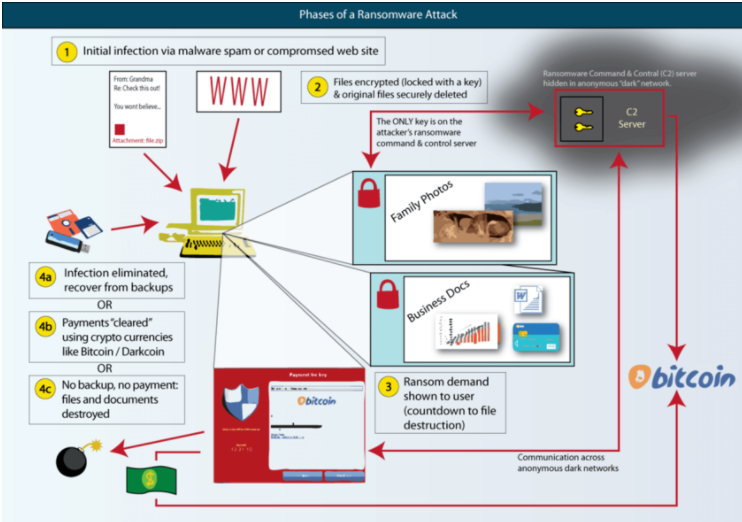
How does ransomware work
The first step in any ransomware attack is getting access to the system. It can happen in a variety of different ways and often depends on who the target is. Malspam and phishing emails are common means of infection. For malware to initiate, all that is necessary to do is for users to open attached malicious files. The emails are often made to look like they come from trusted sources to encourage users to open the files without much thought. Some malspam attempts are more sophisticated than others, with generic ones being quite obvious.
The whole process is quite difficult but the gist of it is that once ransomware is inside a computer, it usually starts encrypting files as soon as possible. During an attack on individual users, personal files (photos, images, videos, documents, etc.) are encrypted. When targetting a business or organization, essential files for the business to operate are usually targeted. More recently, certain ransomware strains started, in addition to file encryption, stealing sensitive information. The cybercriminals operating the ransomware then essentially blackmail the victims by threatening to release the information online if the ransom is not paid.
After ransomware successfully encrypts files, a ransom note is dropped. Generally, the note contains instructions on how the purchase the decryptor and/or contact the cybercriminals operating the malware. Getting the decryptor always involves paying the ransom, though the sum differs from ransomware to ransomware.
Common ransomware targets
Depending on the ransomware and the gang that operates it, victim types are different. While one ransomware may focus on individual users, another may only attack large organizations.
- Regular users
While the big money is in attacks on big organizations, there are many ransomware strains that only target individual users. These infections usually spread via emails or torrents. Ransomware strains targetting random individual users usually demand up to $1000 in ransom.
- Small businesses
In recent years, small businesses have become a common target for ransomware attacks. The logic for that is that they tend to have lax security, either because of insufficient funds or the belief that they will never be targeted. Ransom demands are usually what small businesses would be able to pay.
- Large organizations/businesses
Large organizations and businesses, as well as government organizations, are often a tempting target for ransomware operators as that is where the biggest money is. Some organizations are also more likely to pay the ransom to restore operations quickly. For example, organizations in the healthcare sector cannot afford any downtime, thus are a common target.
How to prevent a ransomware attack
There are a couple of essential steps when it comes to preventing a ransomware infection, or at least lessening the damage an attack could cause.
- File backup
The most important thing to do is regularly make backups. Not just because of ransomware, backing up all important files is critical for anyone who does not wish to lose them. There are multiple ways to back them up, including cloud services and external hard drives. It’s best to set up automatic backups but in the worst-case scenario, manually backing up is also an option.
- Anti-virus software
Anti-virus software is the one thing that often stands between malware and a computer. It’s important to choose a reliable anti-virus program that has protection against ransomware. Anti-virus software is essential to less tech-savvy users in particular, as they are less likely to recognize potential malware attacks.
- Updates
The WannaCry ransomware attack proved the importance of installing updates. System and software vulnerabilities are often used by malware to infect computers and known vulnerabilities are patched by updates. Thus, installing an update could prevent a serious malware attack. If possible, it’s recommended to set up automatic updates.
- Becoming familiar with the common ransomware distribution methods
In many cases, it’s not difficult to recognize a potential malware attack, users just need to know what to look for. Regular ransomware attacks are often initiated by users opening malicious email attachments or torrent files, so if users learn what that looks like, they should be able to avoid it.
Ransomware removal
The best course of action when dealing with ransomware infections is to use anti-malware software. Ransomware is a highly complicated infection and trying to manually remove it could result in more damage. It’s also much easier to use anti-malware software.
Unfortunately, removing the ransomware does not decrypt files. The files have been encrypted and it’s not possible to open them unless they are first run through a decryptor. However, while removing the ransomware will not decrypt files, it’s an essential step if files are to be recovered from a backup. If the ransomware is still present when the backup is accessed, those files would become encrypted as well.
Why paying the ransom is not recommended
Many victims face the dilemma of whether they should pay the ransom or not when dealing with the aftermath of a ransomware attack. For users who have backed up their files, there is no reason to pay the ransom because they can easily recover files after removing the ransomware. However, for businesses and organizations, using backup is not always the quickest option. Or the cheapest choice. This is the reason why some victims choose to pay the ransom, despite having a backup.
In most cases, both malware specialists and law enforcement recommend against paying the ransom. Generally, there are a couple of reasons for this. One of the biggest reasons, though more applicable to regular users rather than bigger targets, is that cybercriminals do not always provide the decryptors. In other cases, the decryptor may not work as it is supposed to. Though that is often fixable, and victims can turn to specialists to fix the decryptor so it actually decrypts files. It is important for users to remember that ransomware is operated by cybercriminals and there is little to obligate them to help victims. Numerous users in the past paid the ransom only to receive nothing in return. Like we already mentioned, not receiving a decryptor is more common for individual users rather than bigger targets because if a large target does not receive a decryptor, it would discourage other bigger victims from paying the ransom.
Another significant reason why it isn’t a good idea to pay the ransom is that it encourages cybercriminals to continue their malicious activities. This is the main reason law enforcement does not encourage paying. Ransomware operators make a lot of money from ransomware. Some of the biggest ransomware payouts include travel company CWT paying $4.5 million in ransom, and Colonial Pipeline agreeing to pay $4.4 million. The latter was one of the most serious ransomware attacks in history with consequences felt by millions of people in the US. With payouts like this, even if they’re not particularly common, it’s no surprise that cybercriminals choose to perform ransomware attacks.
Interestingly enough, some ransomware operators adjust their ransom demands depending on who they target. It’s not uncommon for targets located in poorer countries to get smaller ransom demands than victims in economically more wealthy countries. Ransomware operators also modify ransom demands to make it worth it for businesses to pay. When it comes to a ransomware attack, it’s important to consider not only the recovery time but also how downtime will impact the business. If recovery from backup takes a while, downtime for a business can have significant financial consequences. Paying the ransom may be cheaper than actually recovering data from a backup. Thus, it’s important for businesses to not only have a backup but also a fast recovery plan so that when an attack happens, they can avoid significant downtime and return to normal operations as fast as possible.
Most famous ransomware attacks
- Colonial Pipeline ransomware attack
On May 7, 2021, the American oil pipeline Colonial Pipeline became the victim of a ransomware attack that crippled all of the pipeline’s operations for a number of days. The ransomware, now known as DarkSide ransomware, targeted the computerized equipment that was used to manage the pipeline. In order to contain the attack, the pipeline halted all of the pipeline’s operations. DarkSide also reportedly stole 100 GB of data, which they threatened to release publicly if the pipeline did not agree to pay the ransom.
Mere hours after the attack, Colonial Pipeline paid the 75 Bitcoin ($4.4 million at the time) ransom. However, the decryptor Colonial Pipeline received was so slow that it was quicker for the pipeline to use its own backups. Fortunately, it appears that the Department of Justice was able to successfully recover 63.7 Bitcoins ($2.3 million at the time).
The attack, or rather the impact, attracted a significant amount of attention from the media and law enforcement. The attention the group behind the attack got was perhaps much bigger than the cybercriminals anticipated, as the group shut down all operations and went dark for a period of time.
- Kaseya ransomware attack
On July 2, 2021, Kaseya, an IT management software company, was the target of a cyberattack that resulted in a number of managed service providers (MSPs) becoming the victim of ransomware attacks, which in turn also affected over 1,000 MSP customers. Soon after reports started coming in that hundreds of companies were dealing with ransomware, Kaseya’s remote monitoring and management software package VSA (Virtual System Administrator) was identified as the source of the outbreak. It soon became clear that a vulnerability allowed cybercriminals, now identified as the REvil gang, to distribute malicious payload through the compromised VSA software. Kaseya infected their managed service provider customers, who then infected their own customers, resulting in over a thousand affected companies that had to deal with ransomware.
The cyber gang demanded a $70 million ransom payment in return for a universal decryptor. It is not exactly known whether Kaseya paid the ransom but the software provider did obtain a working decryptor from an unnamed “trusted third party”.
Similarly to the Colonial Pipeline ransomware attack, this too attracted a lot of attention. Because REvil is suspected to be operating from Russia, US President Biden discussed the incident during a phone call with Russia’s President Putin, threatening to take down the gang’s servers if Russia did not agree to do it itself. Almost two weeks after the attack on Kaseya, REvil’s entire infrastructure disappeared.
- WannaCry ransomware attack
Perhaps one of the most well-known ransomware attacks was WannaCry. In May 2017, WannaCry ransomware managed to spread worldwide, infecting over 300,000 computers. The ransomware used EternalBlue, an exploit developed by the US National Security Agency (NSA), to spread to older, unupdated Windows computers, resulting in over 200,000 victims. The exploit used in this attack was stolen from the NSA the year prior to the attack by a group known as the Shadow Brokers. Microsoft was aware of the exploit and released an update that patched it two months prior to the attack. However, many users, particularly businesses and organizations, that fell victim either did not install the update or were using old Windows OSs that were no longer supported, thus did not receive updates.
The spread of the ransomware was halted within a couple of hours when a security researcher discovered the kill switch. Nonetheless, the damage was already done. The damage was estimated to range from hundreds of millions to billions of dollars. North Korea was officially named to be behind the attack.