Why crypto wallets are often targeted
In recent years, cryptocurrency popularity has skyrocketed, with anyone and everyone now investing in various cryptocurrencies. This has attracted a lot of novice investors who know very little about cybersecurity, as well as cybercriminals who try to take full advantage of that. Less tech-savvy investors are often more susceptible to both investment scams and crypto wallet hacks because they are unaware of how these types of scams work, nor do they properly secure their crypto accounts.
According to the US Federal Trade Commission, from October 2020 to May 2021, consumers have lost more than $80 million to crypto scams. It’s difficult to measure just how much money investors lose to hacked wallets every year but the amount is likely in the millions as well.
There are many ways to steal someone’s cryptocurrency, and one of them is gaining access to someone’s crypto wallet and transferring the funds to accounts controlled by malicious actors. Once a transfer is made, there is no undoing it so if users fail to secure their accounts, they risk losing all of their cryptocurrency.
How hackers access crypto wallets
In order to be able to protect crypto wallets from cyber attacks, it’s important to understand how these attacks happen in the first place. Understanding, and thus avoiding cyber attacks is a much better protection technique than anything else that can be done. There are quite a few ways cybercriminals can try to gain access to a crypto wallet, and the most common attack vectors are:
- Phishing
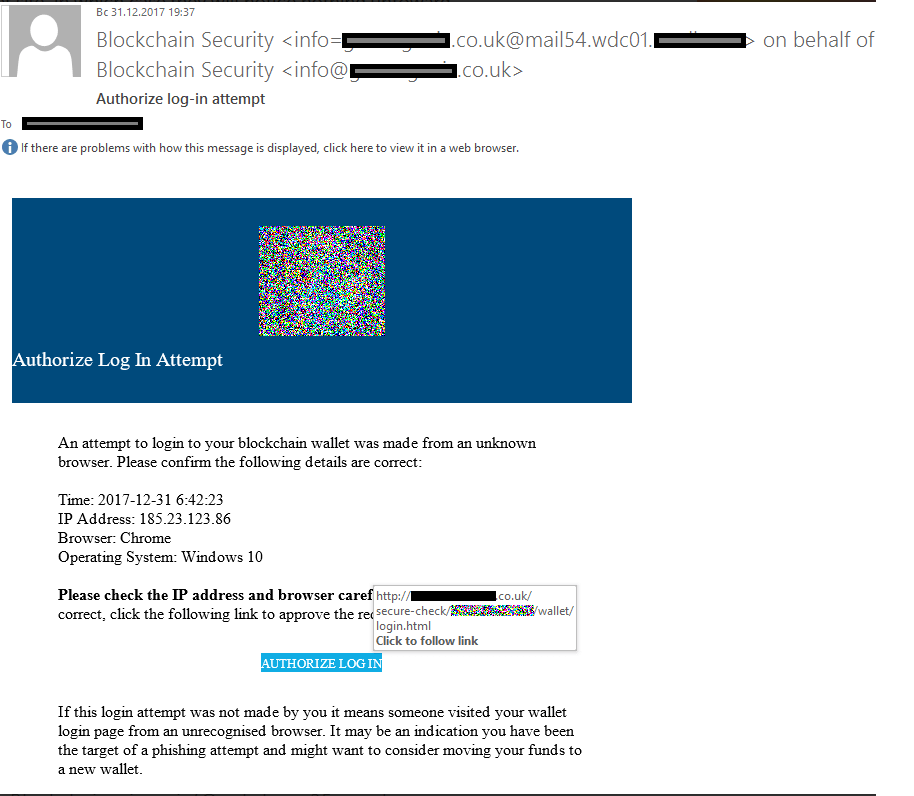
Like in any other kind of cyber attack, phishing is a common way hackers gain access to crypto wallets. A successful phishing attempt would allow cybercriminals to get the necessary login credentials that would grant them access to the wallet and the funds in it. The way a phishing attempt looks differs depending on who the target is. If the goal is stealing crypto wallet login credentials, potential victims may receive emails with links in them, encouraging them to click the link and log in to their wallet for reasons like securing an account. Other phishing attempts may try to trick users into clicking on links and advertisements.
The result is always the same: The victim is directed to a fake version of the expected cryptocurrency site and asked to enter their e-wallet credentials. Most popular Bitcoin Web wallet sites look quite simple, yet recognizable, which helps criminals to create convincing imitations.
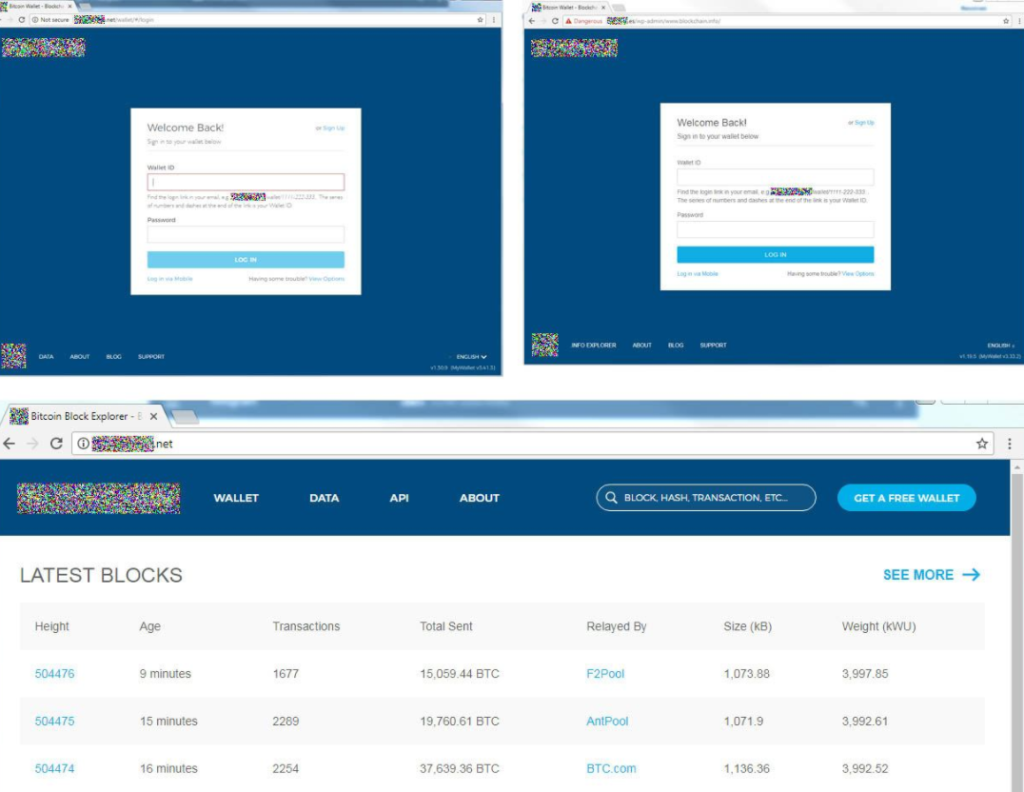
Phishing emails, while quite obvious in most cases, can be very sophisticated, especially when someone is targeted specifically. If cyber crooks can gather information about their potential victim, like a full name and which crypto service they use, the chances of a successful phishing attack go up. Such emails would be made to look like they’re being sent by the crypto service users use and claim that the is some kind of problem with the account. To fix the supposed issue, users would be asked to click on the link and then log in to their account. When users would put in their credentials, they would be sent to the cybercriminals operating the phishing scam.
- SMS 2FA exploits
Two-factor authentication (2FA) is an essential security measure that prevents unauthorized access to an account even when the username and password are known. 2FA is a security process in which users, in addition to a password, need to verify themselves in an additional way, such as inputting a code. This kind of authentication can be done via SMS, special authentication apps, authentication tokens, etc. SMS is one of the most widely used two-factor authentication methods but while it’s better than nothing, SMS 2FA is often susceptible to attacks. This is mostly because of SIM swapping.
SIM swapping is a type of attack that involves cybercriminals convincing phone service providers to assign a certain phone number to a SIM card in their possession. When customers lose or have their phones stolen, they can call their service providers and ask them to transfer the phone number they were using to another SIM. To do this, all that’s necessary is to provide some personal information to the service provider over the phone. This is often exploited by cybercriminals, who first phish users’ personal information and then impersonate them when calling phone service providers. It’s possible to set up PIN numbers that would be asked by service providers when switching SIMs but not many people use this security feature.
If a cybercriminal is able to successfully SIM swap someone’s phone number, they would then receive the 2FA codes to a phone in their possession, allowing them to access crypto wallets that are protected with SMS two-factor authentication.
- Malicious software
Malicious software, or malware, can be used in a variety of ways in crypto wallet hacks. For example, keyloggers can be used to steal crypto wallet login credentials. If a computer is infected with a keylogger, it would record keystrokes (including when login credentials are put in) and then send them to cybercriminals, who would then use them to access the crypto accounts.
Malware can also be used in different ways. Some malicious software can be programmed to automatically replace copied wallet addresses with ones that belong to cybercriminals. For example, when users try to transfer cryptocurrency to another account and copy/paste the wallet address, malware can replace that address with a different one. Less attentive users may not even notice this happening until it’s too late to do anything. This kind of malware may not show any signs of being present on a computer and be quite stealthy.
How you can protect your crypto wallet
- 2FA
As we already mentioned, two-factor authentication adds an additional layer of security to an account by requiring extra verification. Enabling this feature is essential in order to protect a crypto wallet. Nowadays, most crypto services offer 2FA so there is no excuse to not enable it. Ideally, users should use apps or authentication tokens instead of SMS authentication to secure their accounts, especially if their phone numbers are found online without much trouble.
- Monitor transactions
Just with a bank account, it’s important to monitor all transactions in your crypto account. If there are any transactions that seem suspicious, immediate measures to secure the account should be taken, including changing the password and checking the computer for malware.
- Never reuse passwords
If you were to follow one piece of advice when it comes to securing your accounts, it’s to never reuse passwords. Reusing the same password on several different platforms significantly increases the chances of those accounts being breached. If the password ever leaks, hackers would be able to access multiple accounts. Ideally, users should also have a separate email address for crypto accounts.
- Password manager
A good way to be on top of the password game is to have a password manager. They are useful tools that generate strong passwords and store them in one place. They automatically fill in login credentials on websites, and it’s only necessary to remember one password to access the password manager.
- Look into the most common attacks and types regularly
When it comes to crypto scams, it’s better to be proactive than reactive. It’s a good idea to keep up to date with the common scams involving cryptocurrency because it will help avoid becoming a victim if users ever encounter them themselves. There are plenty of resources and sites that provide information about the most recent scams.
- Anti-virus software
In order to protect a crypto wallet, it’s essential to only access it on a secure device. And to secure a device, anti-virus is vital. Malware does not always show signs of being present and only security software may be able to detect it.